2019-11-01 18:51:22 -04:00
|
|
|
// Copyright 2019 The Gitea Authors. All rights reserved.
|
2022-11-27 13:20:29 -05:00
|
|
|
// SPDX-License-Identifier: MIT
|
2019-11-01 18:51:22 -04:00
|
|
|
|
|
|
|
|
package webhook
|
|
|
|
|
|
|
|
|
|
import (
|
2019-12-15 04:51:28 -05:00
|
|
|
"context"
|
2021-06-27 15:21:09 -04:00
|
|
|
"crypto/hmac"
|
|
|
|
|
"crypto/sha1"
|
2019-11-01 18:51:22 -04:00
|
|
|
"crypto/tls"
|
2021-06-27 15:21:09 -04:00
|
|
|
"encoding/hex"
|
2019-11-01 18:51:22 -04:00
|
|
|
"fmt"
|
2021-06-27 15:21:09 -04:00
|
|
|
"io"
|
2019-11-01 18:51:22 -04:00
|
|
|
"net/http"
|
|
|
|
|
"net/url"
|
|
|
|
|
"strings"
|
2019-11-08 16:25:53 -05:00
|
|
|
"sync"
|
2019-11-01 18:51:22 -04:00
|
|
|
"time"
|
|
|
|
|
|
2021-11-10 00:13:16 -05:00
|
|
|
webhook_model "code.gitea.io/gitea/models/webhook"
|
2019-12-15 04:51:28 -05:00
|
|
|
"code.gitea.io/gitea/modules/graceful"
|
2021-11-20 04:34:05 -05:00
|
|
|
"code.gitea.io/gitea/modules/hostmatcher"
|
2019-11-01 18:51:22 -04:00
|
|
|
"code.gitea.io/gitea/modules/log"
|
2022-11-23 09:10:04 -05:00
|
|
|
"code.gitea.io/gitea/modules/process"
|
2021-08-18 09:10:39 -04:00
|
|
|
"code.gitea.io/gitea/modules/proxy"
|
2022-04-25 14:03:01 -04:00
|
|
|
"code.gitea.io/gitea/modules/queue"
|
2019-11-01 18:51:22 -04:00
|
|
|
"code.gitea.io/gitea/modules/setting"
|
2023-05-03 19:53:43 -04:00
|
|
|
"code.gitea.io/gitea/modules/timeutil"
|
2023-01-01 10:23:15 -05:00
|
|
|
webhook_module "code.gitea.io/gitea/modules/webhook"
|
2021-11-10 00:13:16 -05:00
|
|
|
|
2019-11-08 16:25:53 -05:00
|
|
|
"github.com/gobwas/glob"
|
2023-02-22 14:21:46 -05:00
|
|
|
"github.com/minio/sha256-simd"
|
2019-11-01 18:51:22 -04:00
|
|
|
)
|
|
|
|
|
|
|
|
|
|
// Deliver deliver hook task
|
2022-03-31 13:01:43 -04:00
|
|
|
func Deliver(ctx context.Context, t *webhook_model.HookTask) error {
|
2021-11-10 00:13:16 -05:00
|
|
|
w, err := webhook_model.GetWebhookByID(t.HookID)
|
2021-06-27 15:21:09 -04:00
|
|
|
if err != nil {
|
|
|
|
|
return err
|
|
|
|
|
}
|
|
|
|
|
|
2020-05-14 20:06:00 -04:00
|
|
|
defer func() {
|
|
|
|
|
err := recover()
|
|
|
|
|
if err == nil {
|
|
|
|
|
return
|
|
|
|
|
}
|
|
|
|
|
// There was a panic whilst delivering a hook...
|
2022-11-23 09:10:04 -05:00
|
|
|
log.Error("PANIC whilst trying to deliver webhook task[%d] to webhook %s Panic: %v\nStacktrace: %s", t.ID, w.URL, err, log.Stack(2))
|
2020-05-14 20:06:00 -04:00
|
|
|
}()
|
2021-06-27 15:21:09 -04:00
|
|
|
|
2019-11-01 18:51:22 -04:00
|
|
|
t.IsDelivered = true
|
|
|
|
|
|
|
|
|
|
var req *http.Request
|
|
|
|
|
|
2021-06-27 15:21:09 -04:00
|
|
|
switch w.HTTPMethod {
|
2019-11-01 18:51:22 -04:00
|
|
|
case "":
|
2022-11-23 09:10:04 -05:00
|
|
|
log.Info("HTTP Method for webhook %s empty, setting to POST as default", w.URL)
|
2019-11-01 18:51:22 -04:00
|
|
|
fallthrough
|
|
|
|
|
case http.MethodPost:
|
2021-06-27 15:21:09 -04:00
|
|
|
switch w.ContentType {
|
2021-11-10 00:13:16 -05:00
|
|
|
case webhook_model.ContentTypeJSON:
|
2021-06-27 15:21:09 -04:00
|
|
|
req, err = http.NewRequest("POST", w.URL, strings.NewReader(t.PayloadContent))
|
2019-11-01 18:51:22 -04:00
|
|
|
if err != nil {
|
|
|
|
|
return err
|
|
|
|
|
}
|
|
|
|
|
|
|
|
|
|
req.Header.Set("Content-Type", "application/json")
|
2021-11-10 00:13:16 -05:00
|
|
|
case webhook_model.ContentTypeForm:
|
2022-01-20 12:46:10 -05:00
|
|
|
forms := url.Values{
|
2019-11-01 18:51:22 -04:00
|
|
|
"payload": []string{t.PayloadContent},
|
|
|
|
|
}
|
|
|
|
|
|
2021-06-27 15:21:09 -04:00
|
|
|
req, err = http.NewRequest("POST", w.URL, strings.NewReader(forms.Encode()))
|
2019-11-01 18:51:22 -04:00
|
|
|
if err != nil {
|
|
|
|
|
return err
|
|
|
|
|
}
|
|
|
|
|
|
|
|
|
|
req.Header.Set("Content-Type", "application/x-www-form-urlencoded")
|
|
|
|
|
}
|
|
|
|
|
case http.MethodGet:
|
2021-06-27 15:21:09 -04:00
|
|
|
u, err := url.Parse(w.URL)
|
2019-11-01 18:51:22 -04:00
|
|
|
if err != nil {
|
2022-11-23 09:10:04 -05:00
|
|
|
return fmt.Errorf("unable to deliver webhook task[%d] as cannot parse webhook url %s: %w", t.ID, w.URL, err)
|
2019-11-01 18:51:22 -04:00
|
|
|
}
|
|
|
|
|
vals := u.Query()
|
|
|
|
|
vals["payload"] = []string{t.PayloadContent}
|
|
|
|
|
u.RawQuery = vals.Encode()
|
|
|
|
|
req, err = http.NewRequest("GET", u.String(), nil)
|
|
|
|
|
if err != nil {
|
2022-11-23 09:10:04 -05:00
|
|
|
return fmt.Errorf("unable to deliver webhook task[%d] as unable to create HTTP request for webhook url %s: %w", t.ID, w.URL, err)
|
2019-11-01 18:51:22 -04:00
|
|
|
}
|
2020-07-30 18:04:19 -04:00
|
|
|
case http.MethodPut:
|
2021-06-27 15:21:09 -04:00
|
|
|
switch w.Type {
|
2023-01-01 10:23:15 -05:00
|
|
|
case webhook_module.MATRIX:
|
2022-11-03 14:23:20 -04:00
|
|
|
txnID, err := getMatrixTxnID([]byte(t.PayloadContent))
|
|
|
|
|
if err != nil {
|
|
|
|
|
return err
|
|
|
|
|
}
|
|
|
|
|
url := fmt.Sprintf("%s/%s", w.URL, url.PathEscape(txnID))
|
|
|
|
|
req, err = http.NewRequest("PUT", url, strings.NewReader(t.PayloadContent))
|
2020-07-30 18:04:19 -04:00
|
|
|
if err != nil {
|
2022-11-23 09:10:04 -05:00
|
|
|
return fmt.Errorf("unable to deliver webhook task[%d] as cannot create matrix request for webhook url %s: %w", t.ID, w.URL, err)
|
2020-07-30 18:04:19 -04:00
|
|
|
}
|
|
|
|
|
default:
|
2022-11-23 09:10:04 -05:00
|
|
|
return fmt.Errorf("invalid http method for webhook task[%d] in webhook %s: %v", t.ID, w.URL, w.HTTPMethod)
|
2020-07-30 18:04:19 -04:00
|
|
|
}
|
2019-11-01 18:51:22 -04:00
|
|
|
default:
|
2022-11-23 09:10:04 -05:00
|
|
|
return fmt.Errorf("invalid http method for webhook task[%d] in webhook %s: %v", t.ID, w.URL, w.HTTPMethod)
|
2021-06-27 15:21:09 -04:00
|
|
|
}
|
|
|
|
|
|
|
|
|
|
var signatureSHA1 string
|
|
|
|
|
var signatureSHA256 string
|
|
|
|
|
if len(w.Secret) > 0 {
|
|
|
|
|
sig1 := hmac.New(sha1.New, []byte(w.Secret))
|
|
|
|
|
sig256 := hmac.New(sha256.New, []byte(w.Secret))
|
|
|
|
|
_, err = io.MultiWriter(sig1, sig256).Write([]byte(t.PayloadContent))
|
|
|
|
|
if err != nil {
|
|
|
|
|
log.Error("prepareWebhooks.sigWrite: %v", err)
|
|
|
|
|
}
|
|
|
|
|
signatureSHA1 = hex.EncodeToString(sig1.Sum(nil))
|
|
|
|
|
signatureSHA256 = hex.EncodeToString(sig256.Sum(nil))
|
2019-11-01 18:51:22 -04:00
|
|
|
}
|
|
|
|
|
|
2021-10-05 13:12:17 -04:00
|
|
|
event := t.EventType.Event()
|
|
|
|
|
eventType := string(t.EventType)
|
2023-01-14 02:16:30 -05:00
|
|
|
req.Header.Add("X-Forgejo-Delivery", t.UUID)
|
|
|
|
|
req.Header.Add("X-Forgejo-Event", event)
|
|
|
|
|
req.Header.Add("X-Forgejo-Event-Type", eventType)
|
|
|
|
|
req.Header.Add("X-Forgejo-Signature", signatureSHA256)
|
2019-11-01 18:51:22 -04:00
|
|
|
req.Header.Add("X-Gitea-Delivery", t.UUID)
|
2021-10-05 13:12:17 -04:00
|
|
|
req.Header.Add("X-Gitea-Event", event)
|
|
|
|
|
req.Header.Add("X-Gitea-Event-Type", eventType)
|
2021-06-27 15:21:09 -04:00
|
|
|
req.Header.Add("X-Gitea-Signature", signatureSHA256)
|
2019-11-01 18:51:22 -04:00
|
|
|
req.Header.Add("X-Gogs-Delivery", t.UUID)
|
2021-10-05 13:12:17 -04:00
|
|
|
req.Header.Add("X-Gogs-Event", event)
|
|
|
|
|
req.Header.Add("X-Gogs-Event-Type", eventType)
|
2021-06-27 15:21:09 -04:00
|
|
|
req.Header.Add("X-Gogs-Signature", signatureSHA256)
|
|
|
|
|
req.Header.Add("X-Hub-Signature", "sha1="+signatureSHA1)
|
|
|
|
|
req.Header.Add("X-Hub-Signature-256", "sha256="+signatureSHA256)
|
2019-11-01 18:51:22 -04:00
|
|
|
req.Header["X-GitHub-Delivery"] = []string{t.UUID}
|
2021-10-05 13:12:17 -04:00
|
|
|
req.Header["X-GitHub-Event"] = []string{event}
|
|
|
|
|
req.Header["X-GitHub-Event-Type"] = []string{eventType}
|
2019-11-01 18:51:22 -04:00
|
|
|
|
2022-11-03 14:23:20 -04:00
|
|
|
// Add Authorization Header
|
|
|
|
|
authorization, err := w.HeaderAuthorization()
|
|
|
|
|
if err != nil {
|
|
|
|
|
log.Error("Webhook could not get Authorization header [%d]: %v", w.ID, err)
|
|
|
|
|
return err
|
|
|
|
|
}
|
|
|
|
|
if authorization != "" {
|
|
|
|
|
req.Header["Authorization"] = []string{authorization}
|
|
|
|
|
}
|
|
|
|
|
|
2019-11-01 18:51:22 -04:00
|
|
|
// Record delivery information.
|
2021-11-10 00:13:16 -05:00
|
|
|
t.RequestInfo = &webhook_model.HookRequest{
|
2021-06-27 15:21:09 -04:00
|
|
|
URL: req.URL.String(),
|
|
|
|
|
HTTPMethod: req.Method,
|
|
|
|
|
Headers: map[string]string{},
|
2019-11-01 18:51:22 -04:00
|
|
|
}
|
|
|
|
|
for k, vals := range req.Header {
|
|
|
|
|
t.RequestInfo.Headers[k] = strings.Join(vals, ",")
|
|
|
|
|
}
|
|
|
|
|
|
2021-11-10 00:13:16 -05:00
|
|
|
t.ResponseInfo = &webhook_model.HookResponse{
|
2019-11-01 18:51:22 -04:00
|
|
|
Headers: map[string]string{},
|
|
|
|
|
}
|
|
|
|
|
|
2022-11-23 09:10:04 -05:00
|
|
|
// OK We're now ready to attempt to deliver the task - we must double check that it
|
|
|
|
|
// has not been delivered in the meantime
|
|
|
|
|
updated, err := webhook_model.MarkTaskDelivered(ctx, t)
|
|
|
|
|
if err != nil {
|
|
|
|
|
log.Error("MarkTaskDelivered[%d]: %v", t.ID, err)
|
|
|
|
|
return fmt.Errorf("unable to mark task[%d] delivered in the db: %w", t.ID, err)
|
|
|
|
|
}
|
|
|
|
|
if !updated {
|
|
|
|
|
// This webhook task has already been attempted to be delivered or is in the process of being delivered
|
|
|
|
|
log.Trace("Webhook Task[%d] already delivered", t.ID)
|
|
|
|
|
return nil
|
|
|
|
|
}
|
|
|
|
|
|
|
|
|
|
// All code from this point will update the hook task
|
2019-11-01 18:51:22 -04:00
|
|
|
defer func() {
|
2023-05-03 19:53:43 -04:00
|
|
|
t.Delivered = timeutil.TimeStampNanoNow()
|
2019-11-01 18:51:22 -04:00
|
|
|
if t.IsSucceed {
|
|
|
|
|
log.Trace("Hook delivered: %s", t.UUID)
|
2022-03-27 23:17:21 -04:00
|
|
|
} else if !w.IsActive {
|
|
|
|
|
log.Trace("Hook delivery skipped as webhook is inactive: %s", t.UUID)
|
2019-11-01 18:51:22 -04:00
|
|
|
} else {
|
|
|
|
|
log.Trace("Hook delivery failed: %s", t.UUID)
|
|
|
|
|
}
|
|
|
|
|
|
2021-11-10 00:13:16 -05:00
|
|
|
if err := webhook_model.UpdateHookTask(t); err != nil {
|
2019-11-01 18:51:22 -04:00
|
|
|
log.Error("UpdateHookTask [%d]: %v", t.ID, err)
|
|
|
|
|
}
|
|
|
|
|
|
|
|
|
|
// Update webhook last delivery status.
|
|
|
|
|
if t.IsSucceed {
|
2023-01-01 10:23:15 -05:00
|
|
|
w.LastStatus = webhook_module.HookStatusSucceed
|
2019-11-01 18:51:22 -04:00
|
|
|
} else {
|
2023-01-01 10:23:15 -05:00
|
|
|
w.LastStatus = webhook_module.HookStatusFail
|
2019-11-01 18:51:22 -04:00
|
|
|
}
|
2021-11-10 00:13:16 -05:00
|
|
|
if err = webhook_model.UpdateWebhookLastStatus(w); err != nil {
|
2019-11-01 18:51:22 -04:00
|
|
|
log.Error("UpdateWebhookLastStatus: %v", err)
|
|
|
|
|
return
|
|
|
|
|
}
|
|
|
|
|
}()
|
|
|
|
|
|
2021-02-11 12:34:34 -05:00
|
|
|
if setting.DisableWebhooks {
|
2021-11-20 04:34:05 -05:00
|
|
|
return fmt.Errorf("webhook task skipped (webhooks disabled): [%d]", t.ID)
|
2021-02-11 12:34:34 -05:00
|
|
|
}
|
|
|
|
|
|
2022-03-27 23:17:21 -04:00
|
|
|
if !w.IsActive {
|
2022-11-23 09:10:04 -05:00
|
|
|
log.Trace("Webhook %s in Webhook Task[%d] is not active", w.URL, t.ID)
|
2022-03-27 23:17:21 -04:00
|
|
|
return nil
|
|
|
|
|
}
|
|
|
|
|
|
2022-03-31 13:01:43 -04:00
|
|
|
resp, err := webhookHTTPClient.Do(req.WithContext(ctx))
|
2019-11-01 18:51:22 -04:00
|
|
|
if err != nil {
|
|
|
|
|
t.ResponseInfo.Body = fmt.Sprintf("Delivery: %v", err)
|
2022-11-23 09:10:04 -05:00
|
|
|
return fmt.Errorf("unable to deliver webhook task[%d] in %s due to error in http client: %w", t.ID, w.URL, err)
|
2019-11-01 18:51:22 -04:00
|
|
|
}
|
|
|
|
|
defer resp.Body.Close()
|
|
|
|
|
|
|
|
|
|
// Status code is 20x can be seen as succeed.
|
|
|
|
|
t.IsSucceed = resp.StatusCode/100 == 2
|
|
|
|
|
t.ResponseInfo.Status = resp.StatusCode
|
|
|
|
|
for k, vals := range resp.Header {
|
|
|
|
|
t.ResponseInfo.Headers[k] = strings.Join(vals, ",")
|
|
|
|
|
}
|
|
|
|
|
|
2021-09-22 01:38:34 -04:00
|
|
|
p, err := io.ReadAll(resp.Body)
|
2019-11-01 18:51:22 -04:00
|
|
|
if err != nil {
|
|
|
|
|
t.ResponseInfo.Body = fmt.Sprintf("read body: %s", err)
|
2022-11-23 09:10:04 -05:00
|
|
|
return fmt.Errorf("unable to deliver webhook task[%d] in %s as unable to read response body: %w", t.ID, w.URL, err)
|
2019-11-01 18:51:22 -04:00
|
|
|
}
|
|
|
|
|
t.ResponseInfo.Body = string(p)
|
|
|
|
|
return nil
|
|
|
|
|
}
|
|
|
|
|
|
2019-11-08 16:25:53 -05:00
|
|
|
var (
|
|
|
|
|
webhookHTTPClient *http.Client
|
|
|
|
|
once sync.Once
|
|
|
|
|
hostMatchers []glob.Glob
|
|
|
|
|
)
|
|
|
|
|
|
2023-10-18 09:07:20 -04:00
|
|
|
func webhookProxy(allowList *hostmatcher.HostMatchList) func(req *http.Request) (*url.URL, error) {
|
2019-11-08 16:25:53 -05:00
|
|
|
if setting.Webhook.ProxyURL == "" {
|
2021-08-18 09:10:39 -04:00
|
|
|
return proxy.Proxy()
|
2019-11-08 16:25:53 -05:00
|
|
|
}
|
|
|
|
|
|
|
|
|
|
once.Do(func() {
|
|
|
|
|
for _, h := range setting.Webhook.ProxyHosts {
|
|
|
|
|
if g, err := glob.Compile(h); err == nil {
|
|
|
|
|
hostMatchers = append(hostMatchers, g)
|
|
|
|
|
} else {
|
|
|
|
|
log.Error("glob.Compile %s failed: %v", h, err)
|
|
|
|
|
}
|
|
|
|
|
}
|
|
|
|
|
})
|
|
|
|
|
|
|
|
|
|
return func(req *http.Request) (*url.URL, error) {
|
|
|
|
|
for _, v := range hostMatchers {
|
|
|
|
|
if v.Match(req.URL.Host) {
|
2023-10-18 09:07:20 -04:00
|
|
|
if !allowList.MatchHostName(req.URL.Host) {
|
|
|
|
|
return nil, fmt.Errorf("webhook can only call allowed HTTP servers (check your %s setting), deny '%s'", allowList.SettingKeyHint, req.URL.Host)
|
|
|
|
|
}
|
2019-11-08 16:25:53 -05:00
|
|
|
return http.ProxyURL(setting.Webhook.ProxyURLFixed)(req)
|
|
|
|
|
}
|
|
|
|
|
}
|
|
|
|
|
return http.ProxyFromEnvironment(req)
|
|
|
|
|
}
|
|
|
|
|
}
|
2019-11-01 18:51:22 -04:00
|
|
|
|
2022-04-25 14:03:01 -04:00
|
|
|
// Init starts the hooks delivery thread
|
|
|
|
|
func Init() error {
|
2019-11-01 18:51:22 -04:00
|
|
|
timeout := time.Duration(setting.Webhook.DeliverTimeout) * time.Second
|
|
|
|
|
|
2021-11-20 04:34:05 -05:00
|
|
|
allowedHostListValue := setting.Webhook.AllowedHostList
|
|
|
|
|
if allowedHostListValue == "" {
|
|
|
|
|
allowedHostListValue = hostmatcher.MatchBuiltinExternal
|
|
|
|
|
}
|
|
|
|
|
allowedHostMatcher := hostmatcher.ParseHostMatchList("webhook.ALLOWED_HOST_LIST", allowedHostListValue)
|
|
|
|
|
|
2019-11-01 18:51:22 -04:00
|
|
|
webhookHTTPClient = &http.Client{
|
2021-11-01 04:39:52 -04:00
|
|
|
Timeout: timeout,
|
2019-11-01 18:51:22 -04:00
|
|
|
Transport: &http.Transport{
|
|
|
|
|
TLSClientConfig: &tls.Config{InsecureSkipVerify: setting.Webhook.SkipTLSVerify},
|
2023-10-18 09:07:20 -04:00
|
|
|
Proxy: webhookProxy(allowedHostMatcher),
|
|
|
|
|
DialContext: hostmatcher.NewDialContextWithProxy("webhook", allowedHostMatcher, nil, setting.Webhook.ProxyURLFixed),
|
2019-11-01 18:51:22 -04:00
|
|
|
},
|
|
|
|
|
}
|
|
|
|
|
|
Improve queue and logger context (#24924)
Before there was a "graceful function": RunWithShutdownFns, it's mainly
for some modules which doesn't support context.
The old queue system doesn't work well with context, so the old queues
need it.
After the queue refactoring, the new queue works with context well, so,
use Golang context as much as possible, the `RunWithShutdownFns` could
be removed (replaced by RunWithCancel for context cancel mechanism), the
related code could be simplified.
This PR also fixes some legacy queue-init problems, eg:
* typo : archiver: "unable to create codes indexer queue" => "unable to
create repo-archive queue"
* no nil check for failed queues, which causes unfriendly panic
After this PR, many goroutines could have better display name:

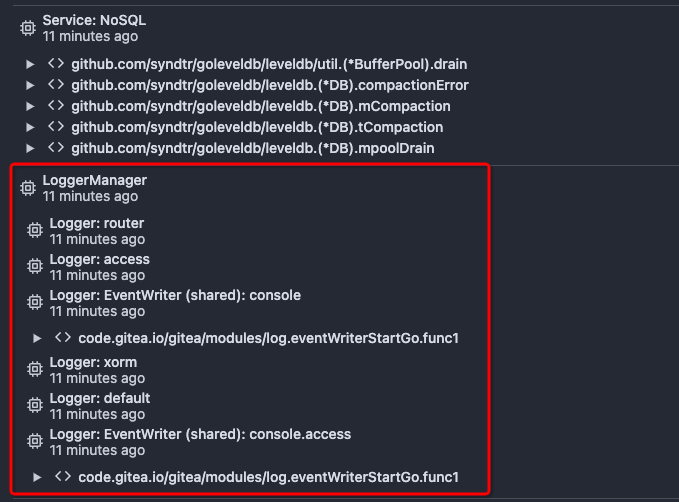
2023-05-26 03:31:55 -04:00
|
|
|
hookQueue = queue.CreateUniqueQueue(graceful.GetManager().ShutdownContext(), "webhook_sender", handler)
|
2022-04-25 14:03:01 -04:00
|
|
|
if hookQueue == nil {
|
Improve queue and logger context (#24924)
Before there was a "graceful function": RunWithShutdownFns, it's mainly
for some modules which doesn't support context.
The old queue system doesn't work well with context, so the old queues
need it.
After the queue refactoring, the new queue works with context well, so,
use Golang context as much as possible, the `RunWithShutdownFns` could
be removed (replaced by RunWithCancel for context cancel mechanism), the
related code could be simplified.
This PR also fixes some legacy queue-init problems, eg:
* typo : archiver: "unable to create codes indexer queue" => "unable to
create repo-archive queue"
* no nil check for failed queues, which causes unfriendly panic
After this PR, many goroutines could have better display name:


2023-05-26 03:31:55 -04:00
|
|
|
return fmt.Errorf("unable to create webhook_sender queue")
|
2022-04-25 14:03:01 -04:00
|
|
|
}
|
Improve queue and logger context (#24924)
Before there was a "graceful function": RunWithShutdownFns, it's mainly
for some modules which doesn't support context.
The old queue system doesn't work well with context, so the old queues
need it.
After the queue refactoring, the new queue works with context well, so,
use Golang context as much as possible, the `RunWithShutdownFns` could
be removed (replaced by RunWithCancel for context cancel mechanism), the
related code could be simplified.
This PR also fixes some legacy queue-init problems, eg:
* typo : archiver: "unable to create codes indexer queue" => "unable to
create repo-archive queue"
* no nil check for failed queues, which causes unfriendly panic
After this PR, many goroutines could have better display name:


2023-05-26 03:31:55 -04:00
|
|
|
go graceful.GetManager().RunWithCancel(hookQueue)
|
2022-04-25 14:03:01 -04:00
|
|
|
|
2022-11-23 09:10:04 -05:00
|
|
|
go graceful.GetManager().RunWithShutdownContext(populateWebhookSendingQueue)
|
|
|
|
|
|
|
|
|
|
return nil
|
|
|
|
|
}
|
|
|
|
|
|
|
|
|
|
func populateWebhookSendingQueue(ctx context.Context) {
|
|
|
|
|
ctx, _, finished := process.GetManager().AddContext(ctx, "Webhook: Populate sending queue")
|
|
|
|
|
defer finished()
|
2022-10-21 12:21:56 -04:00
|
|
|
|
2022-11-23 09:10:04 -05:00
|
|
|
lowerID := int64(0)
|
|
|
|
|
for {
|
|
|
|
|
taskIDs, err := webhook_model.FindUndeliveredHookTaskIDs(ctx, lowerID)
|
|
|
|
|
if err != nil {
|
|
|
|
|
log.Error("Unable to populate webhook queue as FindUndeliveredHookTaskIDs failed: %v", err)
|
|
|
|
|
return
|
|
|
|
|
}
|
|
|
|
|
if len(taskIDs) == 0 {
|
|
|
|
|
return
|
|
|
|
|
}
|
|
|
|
|
lowerID = taskIDs[len(taskIDs)-1]
|
|
|
|
|
|
|
|
|
|
for _, taskID := range taskIDs {
|
|
|
|
|
select {
|
|
|
|
|
case <-ctx.Done():
|
|
|
|
|
log.Warn("Shutdown before Webhook Sending queue finishing being populated")
|
|
|
|
|
return
|
|
|
|
|
default:
|
|
|
|
|
}
|
|
|
|
|
if err := enqueueHookTask(taskID); err != nil {
|
|
|
|
|
log.Error("Unable to push HookTask[%d] to the Webhook Sending queue: %v", taskID, err)
|
|
|
|
|
}
|
2022-10-21 12:21:56 -04:00
|
|
|
}
|
|
|
|
|
}
|
2019-11-01 18:51:22 -04:00
|
|
|
}
|