See:
1b088fade6 Prevent automatic OAuth grants for public clients
07fe5a8b13 use existing oauth grant for public client
(cherry picked from commit 592469464b)
Do not try to create a new authorization grant when one exists already,
thus preventing a DB-related authorization issue.
Fix https://github.com/go-gitea/gitea/pull/30790#issuecomment-2118812426
---------
Co-authored-by: Lunny Xiao <xiaolunwen@gmail.com>
(cherry picked from commit 9c8c9ff6d10b35de8d2d7eae0fc2646ad9bbe94a)
(cherry picked from commit 07fe5a8b13)
This commit forces the resource owner (user) to always approve OAuth 2.0
authorization requests if the client is public (e.g. native
applications).
As detailed in [RFC 6749 Section 10.2](https://www.rfc-editor.org/rfc/rfc6749.html#section-10.2),
> The authorization server SHOULD NOT process repeated authorization
requests automatically (without active resource owner interaction)
without authenticating the client or relying on other measures to ensure
that the repeated request comes from the original client and not an
impersonator.
With the implementation prior to this patch, attackers with access to
the redirect URI (e.g., the loopback interface for
`git-credential-oauth`) can get access to the user account without any
user interaction if they can redirect the user to the
`/login/oauth/authorize` endpoint somehow (e.g., with `xdg-open` on
Linux).
Fixes #25061.
Co-authored-by: wxiaoguang <wxiaoguang@gmail.com>
(cherry picked from commit 5c542ca94caa3587329167cfe9e949357ca15cf1)
(cherry picked from commit 1b088fade6)
It is not possible to tell vulncheck that Forgejo is not affected by
CVE-2024-0406. Use a mirror of the repository to do that.
Refs: https://github.com/mholt/archiver/issues/404
(cherry picked from commit 3bfec270ac)
Conflicts:
go.sum
trivial context conflict
files_service.CreateCommitStatus must not explicitly call
gitRepo.Close(), it will be called by the closer function.
Calling it explicitly will cause the repository to be closed
prematurely when obtained from the context, making it unusuable by the
caller later on.
For instance, as CreateCommitStatus is called indirectly when a
workflow exists for the tag to be created, it will make the repositoryn
in the context unusable for the tag creation API.
It is possible to change some repo settings (its visibility, and
template status) via `git push` options: `-o repo.private=true`, `-o
repo.template=true`.
Previously, there weren't sufficient permission checks on these, and
anyone who could `git push` to a repository - including via an AGit
workflow! - was able to change either of these settings. To guard
against this, the pre-receive hook will now check if either of these
options are present, and if so, will perform additional permission
checks to ensure that these can only be set by a repository owner or
an administrator. Additionally, changing these settings is disabled for
forks, even for the fork's owner.
There's still a case where the owner of a repository can change the
visibility of it, and it will not propagate to forks (it propagates to
forks when changing the visibility via the API), but that's an
inconsistency, not a security issue.
Signed-off-by: Gergely Nagy <forgejo@gergo.csillger.hu>
Agit returned result should be from `ProcReceive` hook but not
`PostReceive` hook. Then for all non-agit pull requests, it will not
check the pull requests for every pushing `refs/pull/%d/head`.
Backport #30104
(cherry picked from commit 6e3aaa997549b83935241e486caf811793c88aea)
Conflicts:
it is implemented differently in Forgejo, just keep the test
in tests/integration/git_push_test.go
Backport #30392
This patch improves the migration from gitbucket to gitea.
The gitbucket uses it's own internal perPage value (= 25) for paging and
ignore per_page arguments in the requested URL. This cause gitea to
migrate only 25 issues and 25 PRs from gitbucket repository. This may
not happens on old gitbucket. But recent gitbucket 4.40 or 4.38.4 has
this problem.
This patch change to use this internally hardcoded perPage of gitbucket
as gitea's maxPerPage numer when migrating from gitbucket. There are
several perPage values in gitbucket like 25 for Isseus/PRs and 10 for
Releases. Some of those API doesn't support paging yet. It sounds
difficult to implement, but using the minimum number among them worked
out very well. So, I use 10 in this patch.
Brief descriptions of problems and this patch are also available in
https://github.com/go-gitea/gitea/issues/30316.
In addition, I'm not sure what kind of test cases are possible to write
here. It's a test for migration, so it requires testing gitbucket server
and gitea server, I guess. Please let me know if it is possible to write
such test cases here. Thanks!
Co-authored-by: Kazushi (Jam) Marukawa <jam@pobox.com>
(cherry picked from commit b6379d2f167551560c870d2d705269c9ba6fc3bc)
Backport #30406
Fix #30378
(cherry picked from commit 55990ebf9240fced8c58491521fc21bf4a4d8f23)
Conflicts:
services/user/delete.go
trivial context conflict because of `[MODERATION] User blocking`
The user that caused the notification to re-evaluates the
schedules is not the one that will trigger the workflows. They are
background tasks that are authored by the action user (id -2).
Such a mis-assignment is problematic when the user that caused the
notification is deleted.
Fixes: https://codeberg.org/forgejo/forgejo/issues/3211
(cherry picked from commit c3e2c25359)
Backport #30175 by @jmlt2002
- Inline math blocks couldn't be preceeded or succeeded by
alphanumerical characters due to changes introduced in PR #21171.
Removed the condition that caused this (precedingCharacter condition)
and added a new exit condition of the for-loop that checks if a specific
'$' was escaped using '\' so that the math expression can be rendered as
intended.
- Additionally this PR fixes another bug where math blocks of the type
'$xyz$abc$' where the dollar sign was not escaped by the user, generated
an error (shown in the screenshots below)
- Altered the tests to accomodate for the changes
Former behaviour (from try.gitea.io):

Fixed behaviour (from my local build):
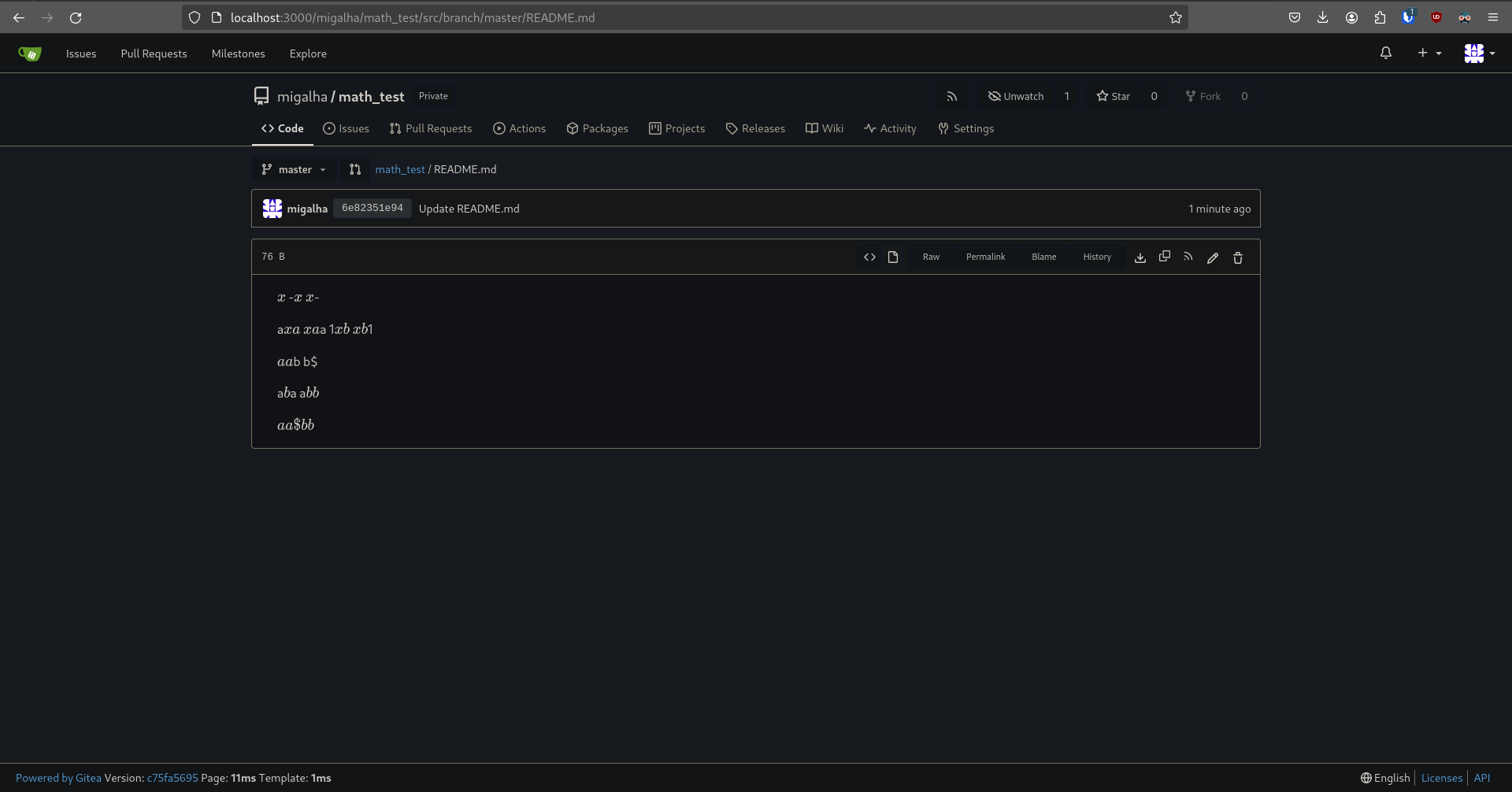
(Edit) Source code for the README.md file:
```
$x$ -$x$ $x$-
a$xa$ $xa$a 1$xb$ $xb$1
$a a$b b$
a$b $a a$b b$
$a a\$b b$
```
Signed-off-by: João Tiago <joao.leal.tintas@tecnico.ulisboa.pt>
Co-authored-by: João Tiago <114936010+jmlt2002@users.noreply.github.com>
(cherry picked from commit 5123ed31914f704348c0660468a3707011f5a160)
Backport #30245 by @KN4CK3R
Fixes #30235
If the key id "front" byte has a single digit, `%X` is missing the 0
prefix.
` 38D1A3EADDBEA9C` instead of
`038D1A3EADDBEA9C`
When using the `IssuerFingerprint` slice `%X` is enough but I changed it
to `%016X` too to be consistent.
Co-authored-by: KN4CK3R <admin@oldschoolhack.me>
(cherry picked from commit 935bfe6445f55f1011782eb93492dc55839b2d16)
Backport #30061 by @wolfogre
Help #29999, or its tests cannot pass.
Also, add some comments to clarify the usage of `TxContext`.
I don't check all usages of `TxContext` because there are too many
(almost 140+). It's a better idea to replace them with `WithTx` instead
of checking them one by one. However, that may be another refactoring
PR.
Co-authored-by: Jason Song <i@wolfogre.com>
(cherry picked from commit 78795dd5663b7d8df4620bd50c74a7d71606f1d2)
Backport #30013 by @DrMaxNix
This PR adds `setting.Service.DefaultOrgMemberVisible` value to dataset
of user when the initial org creator is being added to the created org.
Fixes #30012.
Co-authored-by: DrMaxNix <mail@drmaxnix.de>
(cherry picked from commit e321b8a849087d736a96275d5960f9b1446c95ba)